Key Intake
Q1: Zeeroq.com what is it and why is everyone talking about it?
Zeeroq.com is a defunct cloud service domain that drew attention after being tied to the massive 2024 “Mother of All Breaches,” where millions of reused login credentials surfaced online.
Q2: Why did I get a breach alert about zeeroq.com?
Because your data likely appeared in a repository labeled with that domain, even if you never interacted with the website.
Q3: Is zeeroq.com still online?
No, the domain has been offline since early 2024 and shows no signs of reactivation.
Q4: How can I protect myself if my info was exposed?
Change passwords, enable MFA, and use a password manager. Check Have I Been Pwned to confirm your status.
Q5: Was Zeeroq part of the MOAB breach?
Yes, it was one of thousands of repositories indexed in the 26 billionrecord MOAB dataset discovered in January 2024.
Table of Contents
Quick Answer
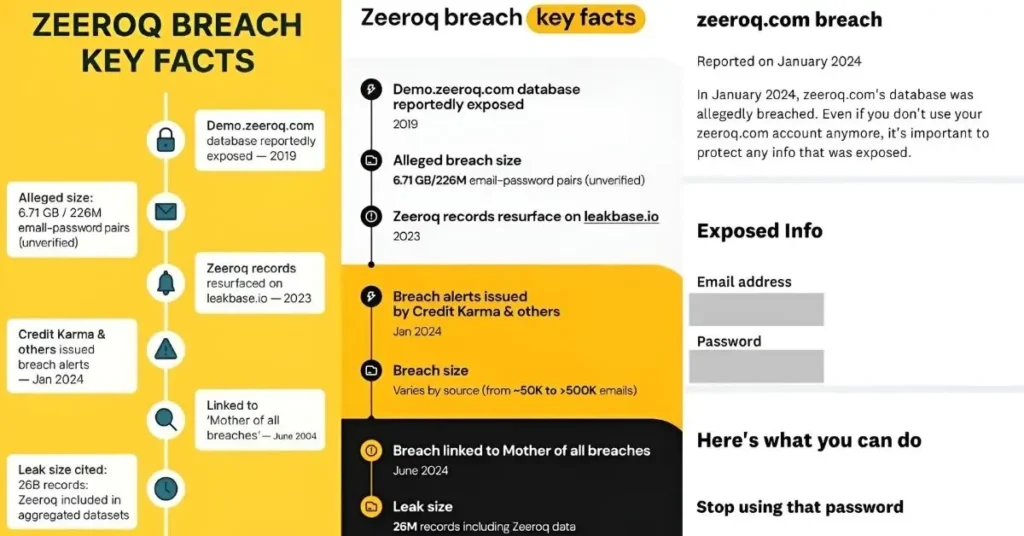
In plain terms, zeeroq.com was a now-defunct cloud services domain that surfaced in the “Mother of All Breaches” (MOAB) dataset, a massive compilation of over 26 billion records leaked online in January 2024.
Contrary to popular belief, Zeeroq wasn’t the hacker. It acted more like a digital warehouse, hosting previously stolen credentials from other companies.
Unlock More Insights
Introduction
In early 2024, millions of people across the U.S. began receiving alarming notifications from cybersecurity monitors like Credit Karma and Have I Been Pwned. The alerts referenced a strange domain named as zeeroq.com, leaving users wondering: “zeeroq.com what is it?” Most had never heard of the site, yet their emails and passwords appeared tied to it. That mystery fueled one of the most confusing cybersecurity stories of the year.
Zeeroq.com what is it? Full info in table
| Attribute | Details about Zeeroq.com |
|---|---|
| Domain Name | Zeeroq.com |
| Operational Status | Defunct, no longer active or accessible as of 2024. |
| Industry Type | Previously linked to cloud-based or digital service hosting, though its exact business model remains uncertain. |
| First Public Mention | Surfaced widely in early 2024, following breach alerts reported by users through Credit Karma and Have I Been Pwned. |
| Incident Overview | Data breach linked to the “Mother of All Breaches” (MOAB), a mega leak that exposed over 26 billion records from thousands of compromised sources. |
| Date of Breach Discovery | January 2024, when users and cybersecurity monitors flagged Zeeroq.com in exposure reports. |
| Scale of Impact | Approximately 50,000 accounts were initially tied to the Zeeroq.com dataset; however, indirect exposure was much broader due to MOAB connections. |
| Type of Data Exposed | Emails, hashed or plaintext passwords, birth dates, and limited payment data, depending on dataset overlap. |
| Breach Attribution | Unclear experts suggest Zeeroq.com’s credentials were aggregated from older leaks and reindexed under its domain. |
| Public Awareness Trigger | Reddit discussions began after multiple users received “Zeeroq.com” breach notifications without having ever interacted with the site. |
| Public Confusion Factor | Users couldn’t identify any past relationship with the site, leading to speculation that Zeeroq.com may have been a dummy domain or data aggregator endpoint. |
| Connection to MOAB (Mother of All Breaches) | Cybersecurity firms like Cybernews and SpyCloud identified Zeeroq-related entries inside MOAB’s 26-billion-record corpus. |
| Company Behind the Domain | No verifiable registration or operating entity publicly confirmed. Domain records show limited WHOIS transparency. |
| Security Measures Taken | None publicly disclosed, domain remained inactive post-incident. |
| Official Statements | No formal press release or company response located. Information primarily derived from security researchers and third-party reports. |
| User Response | High concern and confusion many users sought removal of their data and verification of exposure through breach lookup services. |
| Expert Analysis | Analysts believe Zeeroq.com acted as a collection point or legacy repository, not an actively breached business. |
| Reputation Score (Scamadviser) | Low trust rating, flagged as suspicious or inactive. |
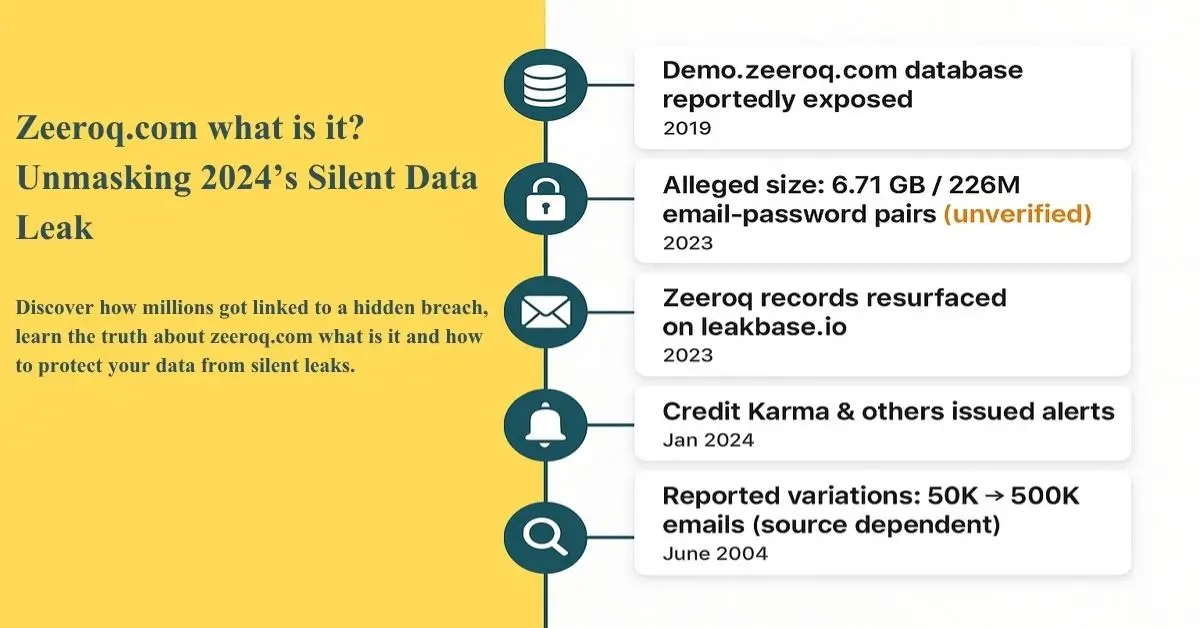
| Related Domains/Subdomains | Historical record shows demo.zeeroq.com referenced in older datasets (circa 2019). |
| Key Sources | Cybernews, SpyCloud Labs, Twingate, OneRep, Reddit cybersecurity threads. |
What Really Happened With Zeeroq.com
The incident started when users saw “zeeroq.com” listed as the breach source in alerts. In truth, the site was a repository , not the original victim. Cyber experts later discovered that the demo.zeeroq.com subdomain contained “combolists”, massive text files bundling email and password pairs reused across multiple services.
The main point: Zeeroq wasn’t necessarily hacked itself. Instead, the domain’s infrastructure was used as a storage layer for recycled breach data. This is why millions received alerts despite never using the site.
Key facts confirmed by analysts:
- The domain was registered in 2008 and changed hands multiple times.
- It became inactive and later repurposed for data-hosting.
- The MOAB dataset referenced Zeeroq as one of thousands of sources.
- No active company statement or verified owner currently exists.
This makes Zeeroq a ghost domain, one that outlived its legitimate purpose and fell into the wrong hands.
If you are not a great fan of reading than, I recommend watching:
→What Is the Zeeroq Data Breach? – SecurityFirstCorp.com
The Scale of Exposure
Cybersecurity firm Twingate estimated that around 50,000 Zeeroq-related account records were found in the leaked dataset. These included names, birth dates, and partial payment details. While small compared to the MOAB’s billions, it was enough to raise panic among ordinary users.
The real danger came from credential reuse. Many of the compromised emails and passwords were duplicates from prior breaches. Attackers could easily plug those combinations into banking, retail, or social accounts, a practice known as credential stuffing.
This is how the Zeeroq issue snowballed from a technical footnote into a personal nightmare for thousands.
Why Did “Zeeroq.com” Show Up in My Breach Alert?

You likely never signed up for Zeeroq, yet it appeared in your data breach report. Here’s why, Platforms like Have I Been Pwned trace the metadata of leaked datasets. When a repository like Zeeroq’s surfaces, its domain gets tagged as the “source label,” even if it wasn’t the original site hacked.
Think of it like a shipping label on stolen cargo, it tells investigators where the data was found, not who it was stolen from.
In this case, “zeeroq.com” became the label for a massive credential dump reused by cybercriminals across multiple platforms.
Zeeroq.com’s Official Response
After public exposure, a statement allegedly linked to Zeeroq claimed that the site had “implemented security enhancements” and worked with experts to patch vulnerabilities. However, cybersecurity communities quickly noted that no verifiable entity stood behind that message. The site itself soon went offline.
Zeeroq’s “response” thus remains more of a placeholder than proof of remediation. No transparency report, audit data, or regulatory filing ever surfaced.
That lack of clarity is what still frustrates consumers, and keeps “zeeroq.com what is it” trending in search engines months later.
How to Check If Your Data Was Involved
Even if you never visited Zeeroq, your credentials could still appear in its dataset. To verify exposure safely, use trusted, non-commercial tools such as:
- HaveIBeenPwned.com: Search your email to see if it appears in Zeeroq or MOAB leaks.
- DeHashed (paid): Cross-check breached credentials tied to Zeeroq.com.
- Mozilla Monitor: Free alerts for new breaches tied to your accounts.
If your data shows up, don’t panic, take action immediately.
What To Do If Your Data Appears Linked to Zeeroq.com

Security experts advise these critical steps:
1. Change Your Passwords Immediately:
Use strong, unique passwords for every site. Avoid reusing the same one across platforms.
2.Enable Multi-Factor Authentication (MFA):
MFA blocks 99% of automated login attempts, according to Microsoft data.
3. Monitor Financial Statements:
Watch for unexpected charges or account activity. Contact your bank if anything seems off.
4. Freeze Your Credit:
In the U.S., you can freeze credit reports through Equifax, Experian, or TransUnion for free.
5.Use a Password Manager:
Tools like Bitwarden, 1Password, or NordPass generate and store secure credentials.
6. Stay Updated:
Follow credible cyber alerts from CISA, KrebsOnSecurity, or your email provider’s security center.
These small moves significantly reduce your risk of identity theft, regardless of whether Zeeroq was your direct breach source.
Lessons From the Zeeroq Incident
Zeeroq’s rise and disappearance highlight a growing issue in the cybersecurity landscape: abandoned or recycled domains becoming data leak amplifiers.
For businesses, it’s a reminder that:
- Domains must be monitored post-sale to prevent misuse.
- Old cloud assets should be decommissioned securely.
- Transparency and early communication matter silence erodes trust faster than breaches.
For individuals, the takeaway is simpler: proactive digital hygiene beats reactive damage control. Reused passwords, neglected MFA, and unmonitored accounts create the perfect storm for exploitation.
The Bigger Picture: A Warning for 2025 and Beyond
The Zeeroq.com case isn’t an isolated event. It’s a symptom of how data brokerage, credential leaks, and forgotten infrastructure intersect. As AI-powered data scrapers grow more advanced, even defunct sites can resurface as part of new breaches.
Experts warn that 2025 will bring a surge of “ghost domain” incidents, where attackers recycle inactive web assets to host stolen datasets. Zeeroq.com is simply the first high-profile example most consumers noticed.
For journalists and SOC teams, Zeeroq serves as a case study in data provenance ambiguity, how easily the “breach source” label can mislead the public when dataset metadata is incomplete.
Sources
To ensure accuracy and depth, this article draws on verified investigations and expert analyses from reputable cybersecurity outlets and research institutions. Key references include:
- Cybernews Research Team: Detailed breakdown of the Mother of All Breaches (MOAB) and how Zeeroq.com surfaced as a secondary repository.
- Twingate Team: Provided technical insights on how Zeeroq.com aggregated leaked credentials and why it wasn’t the original breach source.
- SpyCloud Labs: Analyzed the MOAB dataset and linked Zeeroq’s exposed subdomain to credential reuse patterns across multiple services.
- InsecureWeb Team: One of the earliest public confirmations that Zeeroq.com hosted combolists from previous hacks.
- OneRep Security Team: Issued consumer protection guidance on how to secure accounts and monitor identity exposure following the Zeeroq-related alerts.
Conclusion
In the end, the mystery behind zeeroq.com reminds us how fragile digital privacy can be when data circulates through shadowy corners of the web. For anyone still wondering “zeeroq.com what is it?”, the answer is clear that:
“It wasn’t a major tech platform or a hacking mastermind, but a forgotten domain that became an unwilling symbol of the internet’s recycling of stolen credentials.“
Its story underscores one powerful truth: online security isn’t about who gets breached next, but about who stays prepared.
Author Bio
Samantha R. Vale isa Cyber Threat Analyst with 8 years in digital forensics and breach response. She helps businesses and consumers navigate complex privacy incidents and mitigate exposure risks.